LDAP: различия между версиями
(→LDAP Authentication for Windows 2000) |
(→LDAP Authentication for Windows 2000) |
||
| Строка 161: | Строка 161: | ||
Admin User: "cn=AdminManager,dc=megacorp,dc=com" | Admin User: "cn=AdminManager,dc=megacorp,dc=com" | ||
Admin password: ******* | Admin password: ******* | ||
| − | + | The "Admin User" and "Admin Pass" are not required for "Map Mode". A bind using the user login/password will take place if the Admin user/ password are omitted. | |
Select radio button "Map Mode" then select "OK". (Panel closes) | Select radio button "Map Mode" then select "OK". (Panel closes) | ||
Select Save + Exit | Select Save + Exit | ||
| Строка 189: | Строка 189: | ||
Links: | Links: | ||
| − | SysAdmin: pGina | + | SysAdmin: pGina |
| + | == Способ 2 == | ||
| + | |||
| + | http://openskateshop.com/index.php?WindowsConfig | ||
| + | |||
| + | pGina Configuration | ||
| + | |||
| + | 1. Get pGina components from https://ninja.9star.com/tech/pGina | ||
| + | 2. Download Ninestar CA cert to desktop: https://ninja.9star.com/public/ninestar-ca.crt | ||
| + | 3. Doubleclick it, click "Install...", click "Place all certificates in the following store" | ||
| + | 4. Click "Browse", click "Show physical stores", click "Trusted Root Certificate Authorities", click "Local Computer", click "OK" | ||
| + | 5. Click "Finish" "OK" etc. | ||
| + | 6. Install PGina... | ||
| + | 7. Install logo (from ninja, with the pGina files) in c:\pGina\logo.bmp | ||
| + | |||
| + | 1. Configure as such: | ||
| + | |||
| + | Login Window: | ||
| + | |||
| + | * Load logo from c:\pGina\logo.bmp | ||
| + | * Set window title: "Ninestar Windows Login" | ||
| + | * Set message of the day to: "Welcome to %machine%. Login with your Ninestar email username and password" | ||
| + | * Click "Hide plugin info" | ||
| + | |||
| + | Locked Window: | ||
| + | |||
| + | * Make sure ALL checkboxes are checked, including "Do not allow password change" and "Allow administrator to unlock"... do not check "Allow any user to unlock..." | ||
| + | |||
| + | Account Interaction: | ||
| + | |||
| + | * Should be fine by default... check "Keep profile" and "Force login", uncheck all else | ||
| + | |||
| + | Domain Interaction: | ||
| + | |||
| + | * Should be fine by default... all unchecked | ||
| + | |||
| + | Advanced: | ||
| + | |||
| + | * Fine, unchecked all | ||
| + | |||
| + | Profile: | ||
| + | |||
| + | * Groups, set "Power Users;Users" | ||
| + | |||
| + | 1. Close Configuration Tool | ||
| + | 2. Install LDAPAuth | ||
| + | 3. Relaunch pGina configuration tool from "Start"->Programs->pGina menu | ||
| + | 4. On Plugin screen, select "Browse", c:\pGina\plugins\ldapauth\ldapauth_plus.dll | ||
| + | 5. Click configure button, and set the following: | ||
| + | |||
| + | * Ldap Method: Map Mode | ||
| + | * Ldap Server: ldap.lan (to use the local ldap, or ldap.9star.com to use the central server (be careful)) | ||
| + | * Use SSL: checked | ||
| + | * Port: 636 | ||
| + | * Admin user: uid=reader,ou=People,dc=9star,dc=com | ||
| + | * Admin password: oakley *this is basically public | ||
| + | * Prepend: uid= | ||
| + | * Append: ou=People,dc=9star,dc=com | ||
| + | |||
| + | 1. Click on "User Configuration" tab | ||
| + | |||
| + | * Admin Groups, add: cn=Admin,ou=Access,dc=9star,dc=com | ||
| + | |||
| + | 1. Click on "Password Configuration" tab | ||
| + | |||
| + | * Check "Disable Change Password" | ||
| + | |||
| + | 1. Click "OK" to save changes.... it takes a second, don't fret | ||
| + | 2. Close pGina configuration tool | ||
| + | 3. Launch pGina Plugin Tester tool | ||
| + | 4. Load plugin, try logging in | ||
| + | 5. If successful, then great! Throw away files you downloaded, and restart the machine. | ||
==Samba and LDAP== | ==Samba and LDAP== | ||
Версия 14:30, 23 августа 2007
OpenLDAP
Содержание
Установка
sudo -s apt-get installl slapd ldap-utils nmap php5-ldap
Настройка OpenLDAP
nano /etc/ldap/slapd.conf
Найдите в файле конфигурации параметр loglevel и измените его значение следующим образом
loglevel 296
Теперь нам нужно получить hesh нашего пароля к slapd. Несмотря на то что мы уже задали пароль доступа к ldap - сменим его
#slappasswd New
B
Настроим ldap на нашу доменную зону
nano /etc/ldap/slapd.conf
# The base of your directory in database #1
suffix "dc=ntc, dc=local"
#suffix "dc=example, dc=com"
# rootdn directive for specifying a superuser on the database. This is needed
# for syncrepl.
rootdn "cn=admin,dc=ntc,dc=local"
rootpw {SSHA}a0D718g9uULdD0u/tbMHA9wRlmgV+OUu
Добавим набор параметров по умолчанию для приложений работающих с LDAP.
nano /etc/ldap/ldap.conf
ldap_version 3 BASE dc=ntc, dc=local URI ldap://192.168.10.25:389
SIZELIMIT 0 TIMELIMIT 0 DEREF never
Создаем базу ldif и импортируем ее в нашь ldap
nano /etc/X11/base.ldif
dn:dc=ntc,dc=local objectClass: dcObject objectClass: organization o:ntc dc:ntc
dn:cn=admin,dc=ntc,dc=local objectClass: organizationalRole cn:admin
Импортируем данные в ldap
#ldapadd -x -W -D cn=admin,dc=ntc,dc=local -d /etc/ldap/base.ldif Enter password: XXXXXX ....
И проверим верно ли были внесены данные в базу ldap
#ldapsearch -x
phpLdapAdmin
Загружаем media:phpldapadmin-1.0.2.zip
Для коректной работы phpmyadmin вам потребуется внести ваши параметры dc в конфигурационный файл.
#nano /var/www/phpldapadmin/config/config.php
Замените все dc=exaples,dc=com на ваши параметры
Для доступа к web интерфейсу управления LDAP нам потребуется сделать символьную ссылку на диреторию с установленным phphldapadmin
#ln -s /usr/share/phpldapadmin /var/www/phpldapadmin
Для доступа используйте
login: cn=admin,dc=ntc,dc=local Password:XXXX
Настройка клиентов
http://www.yolinux.com/TUTORIALS/LDAP_Authentication.html
This will create the file: /etc/ldap.conf
host XXX.XXX.XXX.XXX - IP address of LDAP server base dc=domain,dc=org ssl no pam_password md5
If using older SGI MIPS/IRIX systems in the mix you may have to use "clear" instead of "md5".
File: /etc/nsswitch.conf ..
... passwd files ldap shadow files ldap group files ldap ... ..
[Potential Pitfall]: You may have to reboot in order for LDAP authentication to begin.
[Potential Pitfall]: If using the Sun One LDAP authentication server, note that any entry for the following attributes will result in the requirement that the Linux user change their password each and every time they login. (annoying) Set the following LDAP attributes to blank (not zero): shadowmin shadowmax shadowwarning
[Potential Pitfall]: The user IDs (uid) and group IDs (gid) are cached by the Linux client after authenticating to the LDAP server. If changes are made to the LDAP directory you may have to reboot the client system to pick up the changes. This is also true for NIS authentication.
Note: If using the Linux GUI desktop and mounting Linux home directories to an NFS server you may have to mount with the option "nolock". This will be required if the NFS server does not support rpc.statd or rpc.lockd locking daemons which support NFS file locking services.
File: /etc/fstab
... nfs-server:/export/home /export/home nfs rw,soft,bg,nolock 0 0 ...
Also be sure to copy essential files and directories from /etc/skel/...which enable desktop use.
LDAP Authentication for Windows 2000
Addition:
Authenticate MS/Windows using PGina: http://pgina.xpasystems.com/
Downloads: http://sourceforge.net/project/downloading.php?group_id=53525&use_mirror=kent&filename=pGina-1.8.8.zip&68517626
i.e. download pGina: pGina170a.exe
Run pGina170a.exe to install. Install to C:\pGina and accept defaults.
Download LDAP Auth: Downloads: http://pgina.xpasystems.com/plugins/ldapauth.php Download instaler i.e.: ldapauth12.exe Run to install.
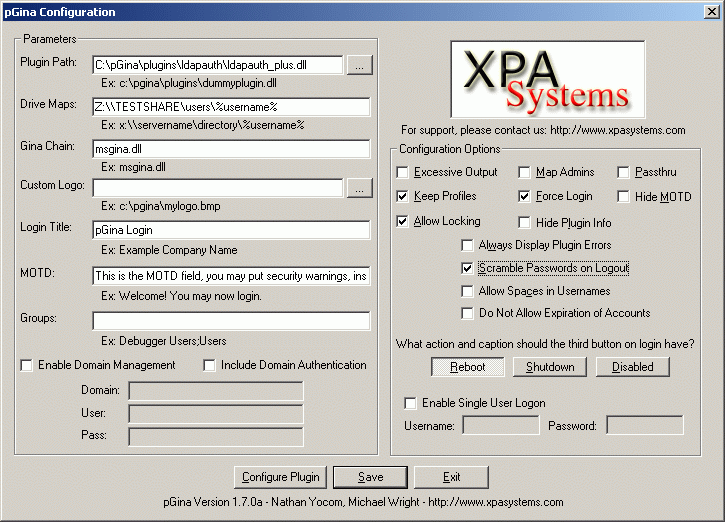
Configure pGina: Select: Start + Programs + pGina + Configuration Tool Pluggin Path: C:\pGina\plugins\ldapauth\ldapauth_plus.dll Accept rest of defaults. Select configure plugin button:
[LDAP configure screenshot] LDAP Server: IP-address-goes-here Port: 389 (default) PrePend: uid= Append: ou=people,dc=megacorp,dc=com Admin User: "cn=AdminManager,dc=megacorp,dc=com" Admin password: *******
The "Admin User" and "Admin Pass" are not required for "Map Mode". A bind using the user login/password will take place if the Admin user/ password are omitted.
Select radio button "Map Mode" then select "OK". (Panel closes) Select Save + Exit (On main config panel) Uses LDAP "Search mode".
Select option "Scramble Passwords on Logout". This forces LDAP authentication for each login. After an initial login, the login/password become resident locally so that subsequent logins are authenticated locally. This option forces a scramble of the password upon logout forcing Windows/pGina to authenticate with the LDAP server and NOT locally.
Optional test: Download plugin_tester.exe from http://pgina.xpasystems.com/plugins/ldapauth.php LDAP_authentication.jpg
Select: Start + PRograms + pGina + Plugin tester Pluggin Path: C:\pGina\plugins\ldapauth\ldapauth_plus.dll Use login and passsword to test.
Reconfigure Windows 2000 not to authenticate against PDC:
- Right click on "My Computer" + System Properties
- Select "Network Identification" tab + "Properties" button.
- Select "Workgroup" radio buton and remove workgroup.
- Reboot and you are ready to login with LDAP authentication.
Note:
Do not use false (which can't be resolved) or a real domain (real or real but fails). pGina recognizes local logins if the login id can not be found in the LDAP directory. pGina does not support "roaming profile". To remove pGina: Start + Control Panel + Add/Remove program + select pGina
Links: SysAdmin: pGina
Способ 2
http://openskateshop.com/index.php?WindowsConfig
pGina Configuration
1. Get pGina components from https://ninja.9star.com/tech/pGina 2. Download Ninestar CA cert to desktop: https://ninja.9star.com/public/ninestar-ca.crt 3. Doubleclick it, click "Install...", click "Place all certificates in the following store" 4. Click "Browse", click "Show physical stores", click "Trusted Root Certificate Authorities", click "Local Computer", click "OK" 5. Click "Finish" "OK" etc. 6. Install PGina... 7. Install logo (from ninja, with the pGina files) in c:\pGina\logo.bmp
1. Configure as such:
Login Window:
* Load logo from c:\pGina\logo.bmp * Set window title: "Ninestar Windows Login" * Set message of the day to: "Welcome to %machine%. Login with your Ninestar email username and password" * Click "Hide plugin info"
Locked Window:
* Make sure ALL checkboxes are checked, including "Do not allow password change" and "Allow administrator to unlock"... do not check "Allow any user to unlock..."
Account Interaction:
* Should be fine by default... check "Keep profile" and "Force login", uncheck all else
Domain Interaction:
* Should be fine by default... all unchecked
Advanced:
* Fine, unchecked all
Profile:
* Groups, set "Power Users;Users"
1. Close Configuration Tool 2. Install LDAPAuth 3. Relaunch pGina configuration tool from "Start"->Programs->pGina menu 4. On Plugin screen, select "Browse", c:\pGina\plugins\ldapauth\ldapauth_plus.dll 5. Click configure button, and set the following:
* Ldap Method: Map Mode * Ldap Server: ldap.lan (to use the local ldap, or ldap.9star.com to use the central server (be careful)) * Use SSL: checked * Port: 636 * Admin user: uid=reader,ou=People,dc=9star,dc=com * Admin password: oakley *this is basically public * Prepend: uid= * Append: ou=People,dc=9star,dc=com
1. Click on "User Configuration" tab
* Admin Groups, add: cn=Admin,ou=Access,dc=9star,dc=com
1. Click on "Password Configuration" tab
* Check "Disable Change Password"
1. Click "OK" to save changes.... it takes a second, don't fret 2. Close pGina configuration tool 3. Launch pGina Plugin Tester tool 4. Load plugin, try logging in 5. If successful, then great! Throw away files you downloaded, and restart the machine.
Samba and LDAP
Samba 3.0 can authenticate using LDAP. Download and compile OpenLDAP (even if you are using Sun ONE or some other LDAP server) and the berkley DB source. These libraries will be required when compiling Samba 3.0 for use with LDAP. Compile Samba with the configure option "--with-ldapsam". (./configure --prefix=/opt/samba --with-ldapsam)
We use pGina for login authentication so that all LDAP security rules are followed. (i.e. password length, duration between changes, reuse of passwords, ...) If MS/Windows authenticating with Samba (which in turn is authenticating with LDAP), then many of the LDAP password rules will not be supported. It is for this reason we use pGina. After SAMBA 3.0.7 was available, many of the rules required and supported in pGina are available using SAMBA and the native MS/Windows login. (i.e. Lockout after 5 failed logins) The login/password is held by the MS/windows OS and will be used when accessing Samba shares. Samba will then authenticate the access to the shared drive using LDAP. This replaces the need for a local Samba password database. (created with smbpasswd) In this configuration we did not use the Samba PDC.
File snippet: smb.conf
... passwd backend = ldapsam: ldap://Ip-address-of-LDAP-server/ ldap admin dn = "cn=sambaadmin, ou=people" ldap suffix = "dc=megacorp,dc=com" ldap user suffix = "ou=people" ...
Note: DNS resolvable names are required for all client and server computers which are part of the Samba domain.
Links: Samba 3.0 LDAP Howto
SGI IRIX/MIPS Authentication and Host Lookup Using LDAP:
IRIX OS releases and LDAP/PAM: IRIX version PAM comments
6.5.21- LDAP support
No PAM support.
6.5.22 LDAP support
Limited PAM support. Many of the utilities and services were not supported by PAM.
6.5.23+ LDAP support
Full PAM support.
IRIX 6.5.21 configuration:
Client configuration file: /var/ns/ldap.conf
; SECURITY security ssl - Options are none or ssl cipher RSA_RC4_40_MD5 domain - An empty domain identifies the local domain ; LDAP server specifications
server XXX.XXX.XXX.XXX - IP address of LDAP server
version 2 - Open LDAP is considered V2 while Sun One considers themselves to be V3
base "dc=sub-Domain,dc=domain,dc=com"
scope subtree - Options are subtree, onelevel or sbase
password-hash {CRYPT}
binddn "cn=AdminManager,dc=sub-Domain,dc=domain,dc=com"
bindpwd secret-password
Note: The "bindpwd" is in clear text and NOT encrypted. When connecting to the server it will use a clear text password. This is required on IRIX 6.5.20. {Potential Pitfall]: If no binddn/bindpwd are supplied in this configuration file, then your whole system is opened up for login without authentication. It may look like you logged in with a password but a correct one will not be required. BEWARE! See "man ldap.conf" for more information. LDAP Server: slapd.conf (Linux: /etc/openldap/slapd.conf) database ldbm
password-hash {CRYPT}
suffix "dc=sub-Domain,dc=domain,dc=com"
rootdn "cn=AdminManager,"dc=sub-Domain,dc=domain,dc=com"
rootpw {CRYPT}yDtKCHnyyDtKC
Notes: Only crypt passwords are allowed in the IRIX implementation. Don't use MD5. Note the associations: Server attribute Client attribute
suffix base rootdn binddn rootpw (crypt) bindpwd (clear text)
Client nsswitch: /etc/nsswitch.conf hosts: ldap files nis dns
passwd: ldap files(compat) [notfound=return] nis
Note:
To reactivate new settings:
[root]# nsadmin flush [root]# nsadmin restart
IRIX 6.5.22+ configuration:
Same as above except that the ldap.conf file location is /etc/ldap.conf and the entries "binddn" and "bindpwd" are not required. The entries in /etc/ldap.conf for IRIX 6.5.22+ resemble those for Linux. Bind is done using anonymous bind.
Sun SOLARIS Authentication and Host Lookup Using LDAP:
Configure with the Sun SOLARIS admin tool: ldapclient
IBM/AIX Authentication and Host Lookup Using LDAP:
System Authentication for AIX (and Linux)
Encryption scheme:
It is important to choose the same encryption scheme across platforms. By default Solaris uses CRYPT (DES: Data Encryption Standard) but allows multiple schemes, Redhat and FreeBSD (V4.2+) use MD5 and Suse uses Blowfish.
Encryption Hash prefix
MD5 $1$ plus 12 character salt followed by encrypted password.
Blowfish (blf) $2$ or $2a$ plus 16 character salt followed by encrypted password.
CRYPT (standard DES) Two character salt at beginning of hash followed by encrypted password. Does NOT start with "$". (No consistent prefix.)
CRYPT (extended DES) Nine character salt at beginning of hash followed by encrypted password. Does NOT start with "$". (No consistent prefix.)
Configuration file where encryprion scheme is set: OS Config file
RedHat Linux /etc/libuser.conf
/etc/pam.d/system-auth
(configured using installation)
FreeBSD /etc/login.conf
/etc/auth.conf
/etc/master.passwd
Solaris /etc/security/policy.conf
See: CRYPT_ALGORITHMS_ALLOW
Multiple encryption schemes allowed concurently.
YoLinux.com LDAP Tutorials:
Deploying OpenLDAP - Directory Installation and configuration (V1.2 and 2.x)
Apache and LDAP authentication
OpenLdap 2.x - SLAPD and LDIF configuration
OpenLdap 1.2 - SLAPD and LDIF configuration
LDAP Authentication and user passwords - Adding password protection to LDAP directory.
(Note: This is authentication for the user to access the LDAP database and not using LDAP to authenticate applications)
OpenLdap 1.2 Group security example - SLAPD and LDIF configuration
Create a new custom object by extending the inetOrgPerson schema
OpenLDAP 2.x Schema Extension to support MS/Outlook, Netscape 4.5+, PAM,.. (GILSE)
LDAP admin support scripts and code snippets
Mapping LDAP inetOrgPerson object attributes to Palm Pilot Desktop CSV exchange file
aWebDap - A simple, flexible web front end supporting multiple domains designed for the non-technical user. My favorite, but hey, I wrote it!!
Настройка клиентских станций на Ubuntu
LDAPClientAuthentication Introduction
This page is intended for anyone who wants to enable an Ubuntu client to authenticate on an existing OpenLDAP server. For more details on the server installation part see OpenLDAPServer.
For authenticating on a Sun Java Enterprise System Directory Server should consult the SunLDAPClientAuthentication page. Installation
Install the following packages: libpam-ldap libnss-ldap nss-updatedb (see InstallingSoftware). Note that you have to enable the universe repositories for this.
libpam-ldap to allows for _authentication_ via LDAP. libnss-ldap allows _session_ information via LDAP. That's why /etc/libnss-ldap.conf /etc/pam_ldap.conf have such similar structures.
During installation, you will be asked the following questions:
*
The address of the LDAP server used. You can also use a fully qualified domain name here. For example: ldap.example.com *
The distinguished name of the search base. For example dc=example,dc=com
*
The LDAP version to use. You usually would choose 3 here. *
If your database requires logging in. You would usually choose no here. *
If you want to make configuration readable/writeable by owner only. A no should be the answer to this. *
A Dialog is displayed explaining it cannot manage nsswitch.conf automatically. Just select OK. *
If you want the local root to be the database admin. You would usually choose yes here. *
Again If your database requires logging in. You would usually choose no here. *
Your root login account. For example: cn=manager,dc=example,dc=com *
Your root password. *
After, a dialog explaining the different encryption methods to specify the encryption method to use before sending your password. exop is usually a good choice.
The above steps might vary a bit depending on the Ubuntu distribution used. When you want to restart the configuration you can use dpkg-reconfigure for both libpam-ldap and libnss-ldap packages.
When finished configuring you will need to double check the data in /etc/libnss-ldap.conf. Especially the 'host' entry which doesn't accept URI. Better is to use the 'uri' entries and comment out the 'host'. Configuration
After the installation of the necessary packages you will need to configure the Name Service and PAM. Name Service
In /etc/nsswitch.conf replace compat with files ldap for both the passwd and group entries so you get something like this:
passwd: files ldap group: files ldap
There is a full example provided in the documentation of libnss-ldap: /usr/share/doc/libnss-ldap/examples/nsswitch.ldap
Now you can test the configuration:
$ getent passwd
or
$ getent group
You should see lines that look like they've come straight out of /etc/passwd. These are the lines 'published' by your LDAP server. If you do, the Name Service (NSS) side of the job is done. If not, check /etc/libnss-ldap.conf for typos.
If your setup requires a password to connect to the LDAP server, don't forget to put that password into /etc/libnss-ldap.secret.
BUG ALERT: Make sure /etc/libnss-ldap.conf has "bind_policy soft". If it's not there, a nasty bug with udev can arise at boot-time.
It's also a good idea to shorten the timeouts there.
Don't use sudo when editing this file or leave it open while testing. If you save with a typo, it could mean that you can't access your server anymore. PAM
Four central files control PAM's use of LDAP: common-account, common-auth, common-password and common-session. They're in /etc/pam.d.
For details, see the pam(7) manpage.
Edit /etc/pam.d/common-account to look like this:
account sufficient pam_ldap.so account required pam_unix.so
Edit /etc/pam.d/common-auth to look like this:
auth sufficient pam_ldap.so auth required pam_unix.so nullok_secure use_first_pass
Edit /etc/pam.d/common-password to look like this:
password sufficient pam_ldap.so password required pam_unix.so nullok obscure min=4 max=8 md5
PAM: Stronger Passwords (Optional)
You might be interested in libpam-cracklib (see InstallingSoftware).
To activate it you'll need to edit /etc/pam.d/common-password:
password required pam_cracklib.so retry=3 minlen=6 difok=3 password sufficient pam_ldap.so use_authtok password required pam_unix.so use_authtok use_first_pass
Edit /etc/pam.d/common-session and add pam_ldap.so, like this:
session optional pam_foreground.so session sufficient pam_ldap.so session required pam_unix.so
PAM: Home directory creation (optional)
Edit the common-session file again:
session required pam_unix.so session required pam_mkhomedir.so skel=/etc/skel/ session optional pam_ldap.so session optional pam_foreground.so
Option: Caching Name Service directories
[(Geert) This needs editing, I can't make it work.] [(Geert) nscd can be used, but didn't work either.]
In order to prevent network slowdown or outage from preventing user name lookup and thus login, use the nss-updatedb package to create a local database of the user names. You first need to populate the database for the first time and then create a scheduled job to update the database at a random time each hour (the random time means that all clients are no hitting the LDAP server simultaneously for updates). Run:
$ sudo nss_updatedb ldap
nss_updatedb is storing the cache in /var/lib/misc/.
Now you need to create a script to update the database randomly.
Create a script called nssupdate.sh in /etc/cron.hourly/ and make it executable. It should contain the following:
#!/bin/bash
LOCK=/var/run/auth-update.cron
[ "$1" != "0" ] && [ -f $LOCK ] && [ -d /proc/"$(cat $LOCK)" ] && exit 0
echo $$ > $LOCK
RANGE=3600
[ "$1" != "" ] && RANGE=$1
SLEEP=$RANDOM
[ "$RANGE" != "0" ] && let "SLEEP %= $RANGE" || SLEEP=0
sleep $SLEEP
go=true
while $go; do
/usr/sbin/nss_updatedb ldap
[ $? -eq 0 ] && go=false
[ "$go" == "true" ] && sleep 10
done
rm $LOCK
exit 0
To make actual use of the cached data you will need to edit /etc/nsswitch.conf like this:
passwd: files ldap [NOTFOUND=return] db group: files ldap [NOTFOUND=return] db
This means:
*
look first in the local files (/etc/passwd and /etc/group) *
if not found, use LDAP *
when LDAP does not have user information, exit and return nothing (this is the [NOTFOUND=return] directive) *
if the LDAP server was not reachable, proceed with using the cached data
https://help.ubuntu.com/community/LDAPClientAuthentication
Дополнительные ссылки
http://linux.mkrovlya.ru/book/export/html/63
Оригинальная статья
http://wiki.ubuntu-forum.de/index.php/OpenLDAP
OpenLDAP
Inhaltsverzeichnis [Verbergen]
1 Allgemeines 2 Installation 3 OpenLDAP konfigurieren 4 phpLDAPadmin 4.1 User in phpLDAPadmin anlegen 4.1.1 OU anlegen 4.1.2 Testperson anlegen 4.2 LDAP im Thunderbird einrichten
[bearbeiten] Allgemeines
OpenLDAP ist ein Verzeichnisdienst wie das ActiveDirectory in der Windows-Server-Welt. OpenLDAP ist dabei frei und kostenfrei erhältlich. An dieser Stelle wird die Konfiguration eines OpenLDAP-Servers für die Verwendung als Adressbuch beschrieben, was aber natürlich lange nicht alles ist, was LDAP kann.
Vorraussetzung für das Tutorial ist, dass Ihr mit nano umgehen könnt und Ubuntu mit Apache2 und PHP5 installiert habt (vorzugsweise Ubuntu 6.06.1 LTS Server).
[bearbeiten]
Installation
Zunächst startet Ihr ein Terminal auf Eurem Server und wechselt in den SuperUser-Modus, damit Ihr nicht dauernd "sudo" vor jedem zweiten Befehl schreiben müsst. sudo -s
Die Quellen in /Etc/apt/sources.list müssen vorab freigeschaltet werden. apt-get install slapd ldap-utils nmap php5-ldap
Das war auch schon die Grundinstallation. Während der Installation von slapd werdet Ihr nach einem Passwort gefragt. Merkt Euch dieses gut! :)
[bearbeiten]
OpenLDAP konfigurieren
Um herauszufinden, ob der Server auch gestartet wurde, benötigt man das eben installierte nmap: nmap localhost | grep ldap
Es sollte nun folgendes angezeigt werden: 389/tcp open ldap
Nun richten wir das Loglevel ein. Der Wert 296 ist für uns ideal, denn dort werden Resultate, Suchfilter und Verbindungsmangement geloggt. nano /etc/ldap/slapd.conf
Sucht (Strg+W) nach dem Stichwort "loglevel" und tragt dort die 296 ein
- Read slapd.conf(5) for possible values
loglevel 296
Nun die Datei speichern (Strg+O).
In der Datei /etc/syslog.conf tragt Ihr nun noch folgendes ein (unten drunter):
- local4.debug /var/log/slapd.log
Als nächstes generieren wir einen SSHA-Schlüssel, den wir gleich brauchen:
- slappasswd
New password: xxxxxx Re-enter new password: xxxxxx {SSHA}4GMPGS/UQTOJ7LdI+iOu7lExQAbpzX6/
Markiert die unterste Zeile und kopiert Euch dies möglichst in die Zwischenablage. (der Key der hier gezeigt wird ist das Passwort: xxxxxx, Euer Key sieht dann ganz anders aus ;))
Nun legen wie die Daten für die Basis des LDAP-Servers fest, indem wir die Datei /etc/ldap/slapd.conf editieren und den Wert "suffix" folgendermaßen verändern:
HINWEIS! Beim Ubuntu-Server sollten hier eigentlich schon die richtigen Angaben drinstehen, sofern diese unter /etc/hostname gesetzt wurden! suffix "dc=meinedomain,dc=local"
Diese Änderungen müssen in der ganzen Datei angepasst werden. Am Ende der Datei fügt Ihr nun die Administrator-Daten ein: rootdn "cn=admin,dc=meinedomain,dc=local" rootpw {SSHA}4GMPGS/UQTOJ7LdI+iOu7lExQAbpzX6/
Anschließend speichert Ihr die Datei (Strg+O) und startet den LDAP-Server neu:
- /etc/init.d/slapd restart
Nun sagen wir den Clients, wo der Server überhaupt ist. Dafür erstellen wir die /etc/ldap/ldap.conf neu mit folgendem Inhalt:
ldap_version 3
URI ldap://192.168.x.x:389
SIZELIMIT 0
TIMELIMIT 0
DEREF never
BASE dc=meinedomain, dc=local
Die URI ist die IP oder Domain Eures Servers! Wenn Ihr einen DNS-Server laufen habt, könnt Ihr hier auch im Stil von "ldap.meinedomain.local" einen Eintrag machen.
Anschließend legen wir die Administrationsdaten an, damit wir uns später auch im Server anmelden können. Erstellt dazu eine Datei namens base.ldif und gebt folgenden Inhalt ein:
- nano base.ldif
Inhalt: dn:dc=meinedomain,dc=local objectClass: dcObject objectClass: organization o: meinedomain dc: meinedomain
dn:cn=admin,dc=meinedomain,dc=local objectClass: organizationalRole cn: admin
Datei speichern (Strg+O).
Nun fügen wir die eben angelegte Datei per ldapadd dem LDAP-Server hinzu:
- ldapadd -x -W -D cn=admin,dc=meinedomain,dc=local -f base.ldif
Enter LDAP Password: xxxxxx adding new entry "dc=meinedomain,dc=local" adding new entry "cn=admin,dc=meinedomain,dc=local"
Es kann sein, dass der Server meldet, dass die Daten schon vorhanden sind, wenn das so ist, könnt Ihr die Meldung ignorieren!
Mit ldapsearch -x können wir die Daten vom Server abfragen:
- ldapsearch -x
- extended LDIF
- LDAPv3
- base <> with scope sub
- filter: (objectclass=*)
- requesting: ALL
- meinedomain.local
dn: dc=meinedomain,dc=local objectClass: dcObject objectClass: organization o: meinedomain dc: meinedomain
- admin, meinedomain.local
dn: cn=admin,dc=meinedomain,dc=local objectClass: organizationalRole cn: admin
- search result
search: 2 result: 0 Success
- numResponses: 3
- numEntries: 2
Die Konfiguration ist damit abgeschlossen. Weiter gehts mit der Installation von phpLDAPadmin! :)
[bearbeiten]
phpLDAPadmin
Das ebenfalls als OpenSource verfügbare Administrationstool phpLDAPadmin kann mit wenigen Handgriffen installiert werden.
- apt-get install phpldapadmin
Anschließend empfiehlt es sich, einen Link zu dem Verzeichnis der Installation zu legen, damit die Administrationsoberfläche bequem erreichbar ist.
- ln -s /usr/share/phpldapadmin /var/www/phpldapadmin
- /etc/init.d/apache2 restart
Nun ist die Administration per http://SERVERADRESSE/phpldapadmin erreichbar.
WICHTIGE INFO ZUM LOGIN: Es hat mich einige graue Haare gekostet bis ich endlich raushatte, wie man sich richtig einloggt, weil es nirgends stand:
Login DN: cn=admin,dc=meinedomain,dc=local Passwort: zuvor vergebenes [bearbeiten] User in phpLDAPadmin anlegen
Ohne jetzt im Detail auf die Funktionsweise eines LDAP-Servers eingehen zu wollen, möchte ich Euch in kurzen Schritten zeigen, wie Ihr einen Testuser anlegen könnt.
Die Grundstruktur ist die Domain, die ist bereits angelegt. Darunter folgt die OU (Organisational Unit), die hier den Namen "people" erhält. Darunter werden erst die eigentlichen User angelegt.
[bearbeiten]
OU anlegen
Klickt rechts im Menü auf:
Anschließend seht Ihr auf der linken Seite ein umfangreiches Menü:
Klickt nun "Organisational Unit" an und auf "Proceed >>".
In der "Container DN" sollte bereits Eure Domain eingetragen sein, wenn nicht, ändert dies entsprechend. Bei Orgisational Unit gebt Ihr "people" ein und klickt auf den anschließend erst klickbaren Button "Proceed >>".
Auf der folgenden Seite bestätigt Ihr das Anlegen der OU mit dem Klick auf "Create Object". [bearbeiten] Testperson anlegen
Klickt nun auf das + vor:
und anschließend auf das aufklappende
Links wählt Ihr nun "Adress Book Entry"
und anschließend wieder auf "Proceed >>" klicken.
Nun tragt Ihr alle Daten ein und klickt anschließen wieder auf "Proceed >>".
Auf der folgenden Seite bestätigt Ihr das Anlegen mit "Create Object".
Das war's! Euer erster User ist angelegt :)
[bearbeiten]
LDAP im Thunderbird einrichten
Um LDAP nun auch sinnvoll zu nutzen, beschreibe ich hier kurz die Einrichtung im Thunderbird 2.x .
Startet Thunderbird und klickt im Menü auf Extras und Einstellungen, anschließend auf das Icon Verfassen und dann auf den Reiter Adressieren.
Wählt LDAP-Verzeichnisdienst aus und klickt auf Bearbeiten...
Klickt auf Hinzufügen
In dem folgenden Fenster gebt Ihr nun dem Kind einen Namen, den Adresse vom Server und ansonsten übernehmt Ihr die Daten die Ihr hier seht (natürlich ist der Domainname zu ändern ;)).
Das war's! Der LDAP-Server ist nun von Thunderbird aus erreichbar. Testen könnt Ihr das, indem Ihr nun mit Ok bestätigt und im Thunderbird selber auf das Icon Adressbuch klickt.
Klickt den Namen Eures Servers an und tippt in das Suchfeld * * ein um alle User zu listen. Wenn Ihr z.B. nach einem Nachnamen sucht, wird dann natürlich nur der User mit dem entsprechenden Nachnamen angezeigt.
Viel Spaß mit Eurem LDAP-Server! :)
Kategorien: Netzwerk | 6.06
Альтернативный способ настройки phpldapadmin
phpLDAPadmin LDAP via web
PhpLDAPadmin (pla) is a software written in PHP for the ammistrazione of serveur LDAP. Currently it supports totally OpenLDAP and partially (single reading) other serveur LDAP like Fedora Directory Serveur, Microsoft Active Directory, Sun Directory Serveur (the writing is experiences them and not head).
PREREQUISITI For the execution pla it demands a web-serveur and PHP with support for extension LDAP. To notice that it is not necessary that pla is installed on the same serveur on which is active LDAP (even if is a frequent solution that can be comfortable).
For how much rigurda PHP, on Debian is necessary to make sure itself to have installed the packages php4 and php4-ldap (on other distributions could be called php and php-ldap). Complimando PHP from sources is necessary to use the option --with-ldap in the configuration.
If the extension php-ldap is not cariata Apache to verify in php.ini that it is present the entry extension=ldap.so and that the directive extension_dir you bring back the directory with the module ldap.so
INSTALLATION Using Debian distributions based it is possible to install pla with the commando: apt-get install phpladpadmin.
The installation from sources is simple since it does not demand no compliazione; it is advised if you want to use the last version and you want to personalize the access from web server.
Pla must be installed in a directory accessible from web, can therefore directly install the rows in /var/www (or /var/www/html) or an other point of the filesystem and to shape Apache opportunely in order to approach to you.
As a result of download delll'ultima the stable version of phpldapadmin-X.X.X.tar.gz (if it is not used pla in production it is possible to decide to use also a development version or quite build every day or the CVS) is possible to scompattare the package with the commando: tar xvfz phpldapadmin-X.X.X.tar.gz
CONFIGURATION Opportune E' to create the configuration rows leaving from the supplied example: cp config.php.example config.php.
Later on it is possible to bring the modifications to the rows config.php as soon as created verifying the presence of the corrected formulations for the access to serveur LDAP
$servers [$i] [“host”] = “localhost”; $servers [$i] [“base”] = “dc=example, dc=tld”;
(To control the configuration of serveur LDAP in the rows sldap.conf that it can be found in /etc/ldap or /etc/openldap/)
An other useful parameter of configuration is:
$servers [$i] [“auth_type”] = “session”;
If used a version of pla recent or you will have to set up the variable one blowfish
$config->custom->session [“blowfish”] = “scrivete_qui_una_stringa”;
If you want to approach with authentication being used a DN, assured you of to set up how much follows in the configuration rows:
// $ldapservers->SetValue ($i, “login”, “attr”, “uid”); $ldapservers->SetValue ($i, “login”, “attr”, “dn”);
ACCESS If Apache is shaped correctly is possible to approach through browser pla, through a link similar to http://localhost/phpldapadmin/
TEMPLATE One of the used feature more than pla is sure the creation of new template objects through that they supply a form for the guided insertion of the attributes.
NOTES Pla is in continuous development, the formulations of the configuration rows could be in the various sintassi from those indicated in relation to the fine-serveur configuration remains however for analogy recognizable.
Infobox data
Tipo Infobox: DESCRIPTION Skill Level: 2 - JUNIOR Author: lotabi Last Modernization: 2005-12-15 21:45: 28 Date of creation: 2005-08-20 11:46: 33 Language: Topic Correlates to you OpenLdap
Installation, configuration and use of OpenLDAP Resources on Internet